# 檔案及目錄加密-Encrypt
# 加密軟體工具
##### Linux
1. [Cryptsetup](https://gitlab.com/cryptsetup/cryptsetup) - 支援 LUKS/plain dm-crypt/loop-AES/TrueCrypt/BitLocker 等加密格式
- [How to Encrypt and Decrypt a Partition in Linux](https://www.linuxshelltips.com/encrypt-partition-linux/)
2. [eCryptFS](https://www.xmodulo.com/encrypt-files-directories-ecryptfs-linux.html)
3. [EncFS](https://www.makeuseof.com/tag/encrypt-dropbox-data-encfs-linux/)
4. [CryFS](https://www.cryfs.org/tutorial/)
5. [VeraCrypt](https://archive.codeplex.com/?p=veracrypt) - 跨平台支援,可移動至其他裝置。
- [How to Encrypt USB Drive on Linux Using VeraCrypt](https://www.linuxbabe.com/desktop-linux/encrypt-usb-drive-linux-using-veracrypt)
##### Windows
1. [AxCrypt](https://key.chtouch.com/ContentView.aspx?P=280)
##### 使用心得
安裝
- EncryptFS 輕易安裝在 CentOS 6.x
- EncFS 可以安裝在 CentOS 6,需透過 EPEL 安裝 fuse-encfs
- CryFS 只支援 Ubuntu
使用方法
` ~/ENCRYPTED-DIR ~/DECRYPTED-DIR`
- 三個軟體幾乎都用一樣的方式,需指定兩個目錄,加密目錄與解密目錄,其中解密目錄是用掛載的,實際檔案是以加密型態的檔案儲存在加密目錄內。
- 在加密目錄裡的檔案與資料夾都是以隨機亂數的名稱存在,檔案內容也都是亂數的隨意組合,要得知加密目錄內有什麼檔案與存取檔案內容,就必須經過解密。
- 加密目錄內的檔案解密步驟,作法三者幾乎一樣,都是透過解密目錄掛載方式,掛載成功後,解密目錄的存取就與一般正常目錄一樣。
- 解密目錄必須透過指令掛載後才能被使用,未被掛載前,這只是一個空目錄,而且不應該存取任何檔案。
- 解密所需的設定檔與加密資訊,三者各有所異。
應用範圍
1. 個人雲端檔案加密。以 Dropbox 為例,將加密目錄設定為 Dropbox 的同步上傳目錄,解密目錄則為本地端的任何一個目錄,例如文件區。平常存取 dropbox 檔案都在文件區內作業,如此這些檔案實際被上傳到 Dropbox 雲端,是以加密型態檔案存在。
2. 檔案多人共用加密。將加密目錄設定在共用的 NFS 目錄(NAS),要存取的 Linux 工作站安裝加密軟體,然後將 NAS 上的加密目錄做解密掛載在本地端目錄,解密掛載時必須通過解密程序,至少會有一組密碼。
其他注意事項
同仁在存取解密目錄裡的檔案時,就與一般正常未加密目錄一樣,甚至可以將它們複製或下載,而複製後的檔案是呈現未加密型態。因此這類加密軟體不適合想避免敏感資料外流的作法。
##### GPG
驗證下載檔案的數位簽名檔
```
[root@db2v9 gpg]# tree
.
├── npp.7.8.8.Installer.exe
├── npp.7.8.8.Installer.exe.sig
└── nppGpgPub.asc
0 directories, 3 files
[root@db2v9 gpg]#
[root@db2v9 gpg]# gpg --verify npp.7.8.8.Installer.exe.sig npp.7.8.8.Installer.exe
gpg: Signature made Sun 28 Jun 2020 11:02:09 PM CST using RSA key ID 8D84F46E
gpg: Can't check signature: No public key
[root@db2v9 gpg]# gpg --import nppGpgPub.asc
gpg: key 8D84F46E: public key "Notepad++ " imported
gpg: Total number processed: 1
gpg: imported: 1 (RSA: 1)
gpg: no ultimately trusted keys found
[root@db2v9 gpg]# gpg --verify npp.7.8.8.Installer.exe.sig npp.7.8.8.Installer.exe
gpg: Signature made Sun 28 Jun 2020 11:02:09 PM CST using RSA key ID 8D84F46E
gpg: Good signature from "Notepad++ "
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: 14BC E436 2749 B2B5 1F8C 7122 6C42 9F1D 8D84 F46E
```
##### 延伸閱讀
- GPG 檔案加解密
- [Linux: HowTo Encrypt And Decrypt Files With A Password](https://www.cyberciti.biz/tips/linux-how-to-encrypt-and-decrypt-files-with-a-password.html)
- [How to easily encrypt a file with GPG on Linux](https://linuxaria.com/howto/how-to-easily-encrypt-a-file-with-gpg-on-linux)
- [Encrypting and decrypting files with password in Linux](https://www.blackmoreops.com/2015/05/07/encrypting-files-with-password/)
- 密碼保護
- [Linux: HowTo Encrypt And Decrypt Files With A Password](https://www.cyberciti.biz/tips/linux-how-to-encrypt-and-decrypt-files-with-a-password.html)
- [7 Tools to Encrypt/Decrypt and Password Protect Files in Linux](https://www.tecmint.com/linux-password-protect-files-with-encryption/)
- LUKS
- [Implementing corporate laptop encryption using LUKS](https://www.redhat.com/en/blog/implementing-corporate-laptop-encryption-using-luks)
- [How to unlock LUKS using Dropbear SSH keys remotely in Linux - nixCraft (cyberciti.biz)](https://www.cyberciti.biz/security/how-to-unlock-luks-using-dropbear-ssh-keys-remotely-in-linux/)
# 加密你的隨身碟 - Cryptsetup
##### 說明
如果你想對某個 USB隨身碟內的資料做加密保護,每次掛載前必須先輸入一組密碼。
##### 開始加密
安裝套件
```shell
sudo apt install cryptsetup
```
插入要加密的隨身碟,並完成掛載,假設為 /dev/sdb。使用 GParted 工具建立一個新磁區 /dev/sdb1,格式為 ext4。拔除隨身碟後再重新插入,如果隨身碟自動被掛載,先以手動方式將它卸載確定隨身碟在沒有被掛載模式下,執行
```shell
sudo cryptsetup --verbose --verify-passphrase luksFormat /dev/sdb1
```
> 詢問是否確定時,必須輸入 大寫 YES。
> 接著需設定一組密碼。
開啟加密磁區,與格式化
- 開啟加密磁區時,必須輸入正確的密碼。
- 加密磁區成功被開啟後,會產生一個新磁碟路徑 `/dev/mapper/`
```shell
sudo cryptsetup luksOpen /dev/sdb1 sdb1
sudo fdisk -l
sudo mkfs.ext4 /dev/mapper/sdb1
sudo tune2fs -m 0 /dev/mapper/sdb1
```
如果想對加密磁區加上標籤
```shell
sudo e2label /dev/mapper/sdb1 MyCCWallet
```
到這裡,已經完成加密程序。測試手動掛載,並嘗試寫入資料。
```shell
sudo mkdir /mnt/encrypted
sudo mount /dev/mapper/sdb1 /mnt/encrypted
sudo touch /mnt/encrypted/test.txt
```
測試沒問題後,就可以將加密磁區關閉。
```shell
sudo umount /dev/mapper/sdb1
sudo cryptsetup luksClose sdb1
```
##### Linux Mint 桌面測試
隨身碟在經過加密後,當每次插上 Linux Mint 電腦時,桌面會自動詢問解鎖密碼,在輸入正確密碼後,就可以像一般方式那樣直接存取隨身碟裡的檔案。
[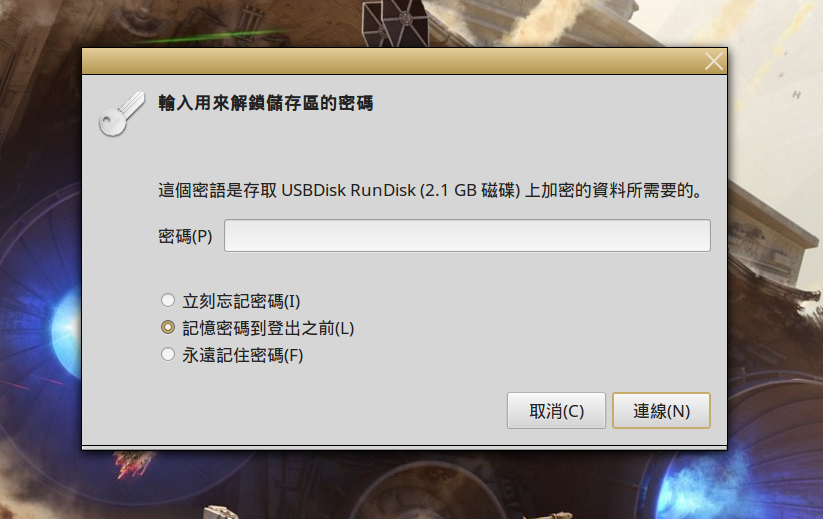](http://www.osslab.tw/uploads/images/gallery/2020-12/ask_password.png)
##### Optional: 其他指令
How to find and verify which Luks slot a passphrase is in on Linux
```shell
# Do not activate device, just check
sudo cryptsetup --verbose open --test-passphrase /dev/vda3
Enter passphrase for /dev/vda3:
Key slot 0 unlocked.
Command successful.
```
##### Learning Cryptsetup
- [How to change LUKS disk encryption passphrase in Linux](https://www.cyberciti.biz/security/how-to-change-luks-disk-encryption-passphrase-in-linux/)
- [Create an encrypted file vault on Linux](https://opensource.com/article/21/4/linux-encryption)
# Learning
##### GPG
- [Using GPG to Encrypt and Decrypt Files on Linux \[Hands-on for Beginners\]](https://itsfoss.com/gpg-encrypt-files-basic/)
##### LUKS
- [How to unlock LUKS using Dropbear SSH keys remotely in Linux - nixCraft (cyberciti.biz)](https://www.cyberciti.biz/security/how-to-unlock-luks-using-dropbear-ssh-keys-remotely-in-linux/)
- [Linux Hard Disk Encryption With LUKS \[cryptsetup command \] - nixCraft (cyberciti.biz)](https://www.cyberciti.biz/security/howto-linux-hard-disk-encryption-with-luks-cryptsetup-command/)
# OpenSSL
Create Example Reference File, let us create a 1GB large text file using the fallocate command:
```shell
fallocate -l 1024M test.txt
echo "LinuxShellTips tutorial on encrypting a large file with OpenSSL in Linux" >> test.txt
cat test.txt
```
##### Encrypt File with Password (對稱式加密)
```shell
openssl enc -aes-256-cbc -pbkdf2 -p -in test.txt -out test.txt.enc
```
- enc executes the symmetric key encryption process.
- -aes-256-cbc specifies the use of 256 bits cryptographic key.
- -pbkdf2 is the default algorithm being used.
- -p prints used salt, key, and IV.
- -in points to the input file.
- -out points to the output file.
To decrypt the file, run:
```shell
openssl aes-256-cbc -d -pbkdf2 -in test.txt.enc -out sample_decrypted.txt
```
> You will be required to enter the encryption password you generated earlier.
##### Encrypt File with Key (對稱式加密)
```shell
# generate a key file
openssl rand 256 > symmetric_keyfile.key
# use the keyfile to encrypt our file
openssl enc -in test.txt -out test.txt.enc -e -aes-256-cbc -pbkdf2 -k symmetric_keyfile.key
```
To decrypt the file, run:
```shell
openssl enc -in test.txt.enc -out draft_decrypted.txt -d -aes-256-cbc -pbkdf2 -k symmetric_keyfile.key
```
##### 非對稱式加密 (Asymmetric Encryption)
使用非對稱式加密對一個大檔案進行加密,可能遇到錯誤: data too large for key size.
[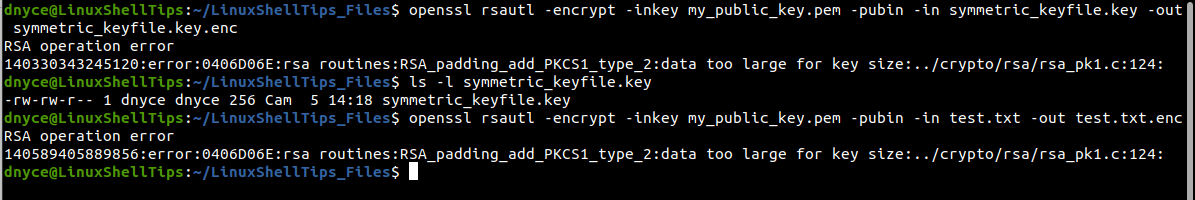](https://osslab.tw/uploads/images/gallery/2022-07/data-too-large-for-key-size.png)
> TIP: 非對稱加密又稱公鑰加密。在使用前要準備好一對私鑰與公鑰,使用公鑰進行檔案的加密,解密時則使用私鑰,操作上較複雜,但是安全性較佳。
##### Hashing
檔案校驗
```bash
# For file
openssl dgst -sha256 my.file
# For string
echo -n "HelloWorld" | openssl dgst -sha256
```
##### 參考網站
- [OpenSSL 對稱式、非對稱式加密檔案指令教學與範例](https://officeguide.cc/linux-openssl-file-symmetic-asymmetric-encryption-commands-tutorial-examples/)