Suricata
Introduction
Suricata is a high performance, open source network analysis and threat detection software used by most private and public organizations, and embedded by major vendors to protect their assets.
Suricata is far more than an IDS/IPS.
Suricata features
There are three main ways Suricata can be used:
-
Intrusion detection system (IDS): As a network-based IDS, Suricata can monitor network traffic and alert on suspicious activities and intrusions. Suricata can also be set up as a host-based IDS to monitor the system and network activities of a single host like a computer.
-
Intrusion prevention system (IPS): Suricata can also function as an intrusion prevention system (IPS) to detect and block malicious activity and traffic. Running Suricata in IPS mode requires additional configuration such as enabling IPS mode.
-
Network security monitoring (NSM): In this mode, Suricata helps keep networks safe by producing and saving relevant network logs. Suricata can analyze live network traffic, existing packet capture files, and create and save full or conditional packet captures. This can be useful for forensics, incident response, and for testing signatures. For example, you can trigger an alert and capture the live network traffic to generate traffic logs, which you can then analyze to refine detection signatures.
Rules (Signatures)
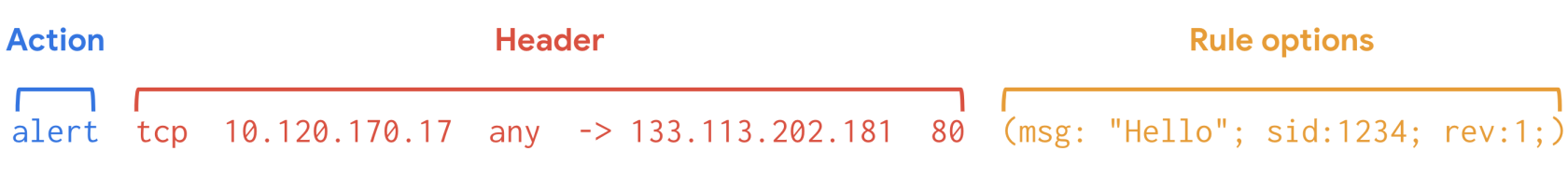
Suricata uses signatures analysis, which is a detection method used to find events of interest. Signatures consist of three components:
-
Action: The first component of a signature. It describes the action to take if network or system activity matches the signature. Examples include: alert, pass, drop, or reject.
-
Header: The header includes network traffic information like source and destination IP addresses, source and destination ports, protocol, and traffic direction.
-
Rule options: The rule options provide you with different options to customize signatures.
Here's an example of a Suricata signature: