nmap 常用指令集
掃描單一主機
### Scan a single ip address ###
nmap 192.168.1.1
## Scan a host name ###
nmap server1.cyberciti.biz
## Scan a host name with more info###
nmap -v server1.cyberciti.biz
掃描多個主機
nmap 192.168.1.1 192.168.1.2 192.168.1.3
## works with same subnet i.e. 192.168.1.0/24
nmap 192.168.1.1,2,3
## You can scan a range of IP address too:
nmap 192.168.1.1-20
## You can scan a range of IP address using a wildcard:
nmap 192.168.1.*
## you scan an entire subnet:
nmap 192.168.1.0/24
# Ping scan subnet
nmap -sP 10.15.9.0/24 | grep -E '\b(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?\.){3}(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)'
nmap -sP 10.15.9.0/24 | sed -n '/^.* [0-9]*\.[0-9]*\.[0-9]*\.[0-9]*/p' | sed 's/^.* \([0-9]*\.[0-9]*\.[0-9]*\.[0-9]*\).*$/\1 /g'
從檔案讀入 IP 清單
nmap -iL /tmp/ip.txt
排除 IP 的方法
nmap 192.168.1.0/24 --exclude 192.168.1.5
nmap 192.168.1.0/24 --exclude 192.168.1.5,192.168.1.254
nmap -iL /tmp/scanlist.txt --excludefile /tmp/exclude.txt
偵測遠端的作業系統類型
nmap -A 192.168.1.254
nmap -v -A 192.168.1.1
nmap -A -iL /tmp/scanlist.txt
偵測遠端主機是否有防火牆
nmap -A 192.168.1.254
nmap -v -A 192.168.1.1
nmap -A -iL /tmp/scanlist.txt
掃描主機(有防火牆保護時)
nmap -PN 192.168.1.1
nmap -PN server1.cyberciti.biz
掃描 IPv6 主機
nmap -6 IPv6-Address-Here
nmap -6 server1.cyberciti.biz
nmap -6 2607:f0d0:1002:51::4
nmap -v A -6 2607:f0d0:1002:51::4
掃描一個子網路內有哪些主機/裝置
nmap -sP 192.168.1.0/24
執行快速掃描
nmap -F 192.168.1.1
顯示通訊埠狀態原因(Reason)
nmap --reason 192.168.1.1
顯示開啟中的通訊埠
nmap --open 192.168.1.1
顯示已傳送/接收的封包
nmap --packet-trace 192.168.1.1
顯示本機網路介面裝置與路由
nmap --iflist
掃描指定通訊埠
nmap -p [port] hostName
## Scan port 80
nmap -p 80 192.168.1.1
## Scan TCP port 80
nmap -p T:80 192.168.1.1
## Scan UDP port 53
nmap -p U:53 192.168.1.1
## Scan two ports ##
nmap -p 80,443 192.168.1.1
## Scan port ranges ##
nmap -p 80-200 192.168.1.1
## Combine all options ##
nmap -p U:53,111,137,T:21-25,80,139,8080 192.168.1.1
nmap -p U:53,111,137,T:21-25,80,139,8080 server1.cyberciti.biz
nmap -v -sU -sT -p U:53,111,137,T:21-25,80,139,8080 192.168.1.254
## Scan all ports with * wildcard ##
nmap -p "*" 192.168.1.1
## Scan top ports i.e. scan $number most common ports ##
nmap --top-ports 5 192.168.1.1
nmap --top-ports 10 192.168.1.1
快速掃描網路內有開啟通訊埠的主機/裝置
nmap -T5 192.168.1.0/24
Cheat Sheet
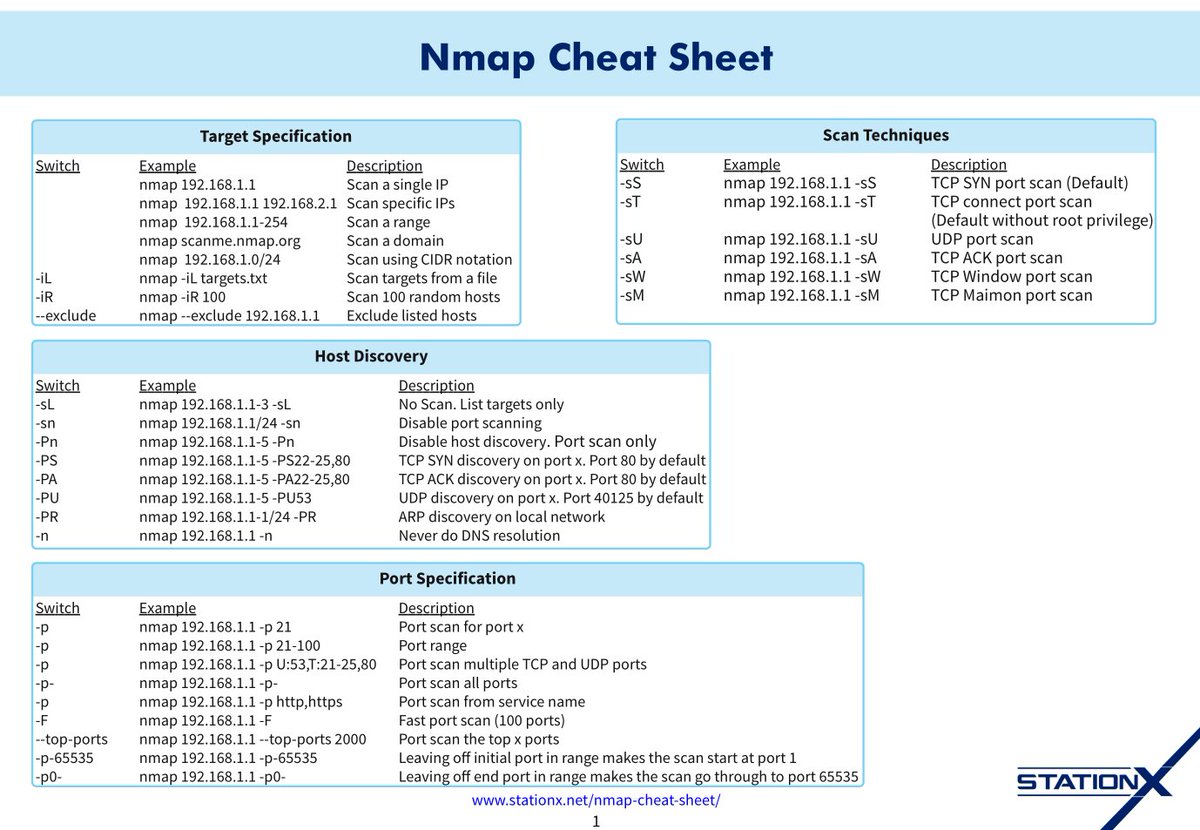


No Comments